Key retrieval agent for OpenStack instances.
This commit was bulk generated and pushed by the OpenDev sysadmins as a part of the Git hosting and code review systems migration detailed in these mailing list posts: http://lists.openstack.org/pipermail/openstack-discuss/2019-March/003603.html http://lists.openstack.org/pipermail/openstack-discuss/2019-April/004920.html Attempts have been made to correct repository namespaces and hostnames based on simple pattern matching, but it's possible some were updated incorrectly or missed entirely. Please reach out to us via the contact information listed at https://opendev.org/ with any questions you may have. |
||
|---|---|---|
| debian | ||
| doc/source | ||
| docs | ||
| etc/marshal | ||
| marshal_agent | ||
| tmp | ||
| .coveragerc | ||
| .gitignore | ||
| .gitreview | ||
| .mailmap | ||
| .testr.conf | ||
| babel.cfg | ||
| CONTRIBUTING.rst | ||
| HACKING.rst | ||
| LICENSE | ||
| MANIFEST.in | ||
| openstack-common.conf | ||
| README.md | ||
| README.rst | ||
| requirements.txt | ||
| setup.cfg | ||
| setup.py | ||
| test-requirements.txt | ||
| tox.ini | ||
Marshal
Overview
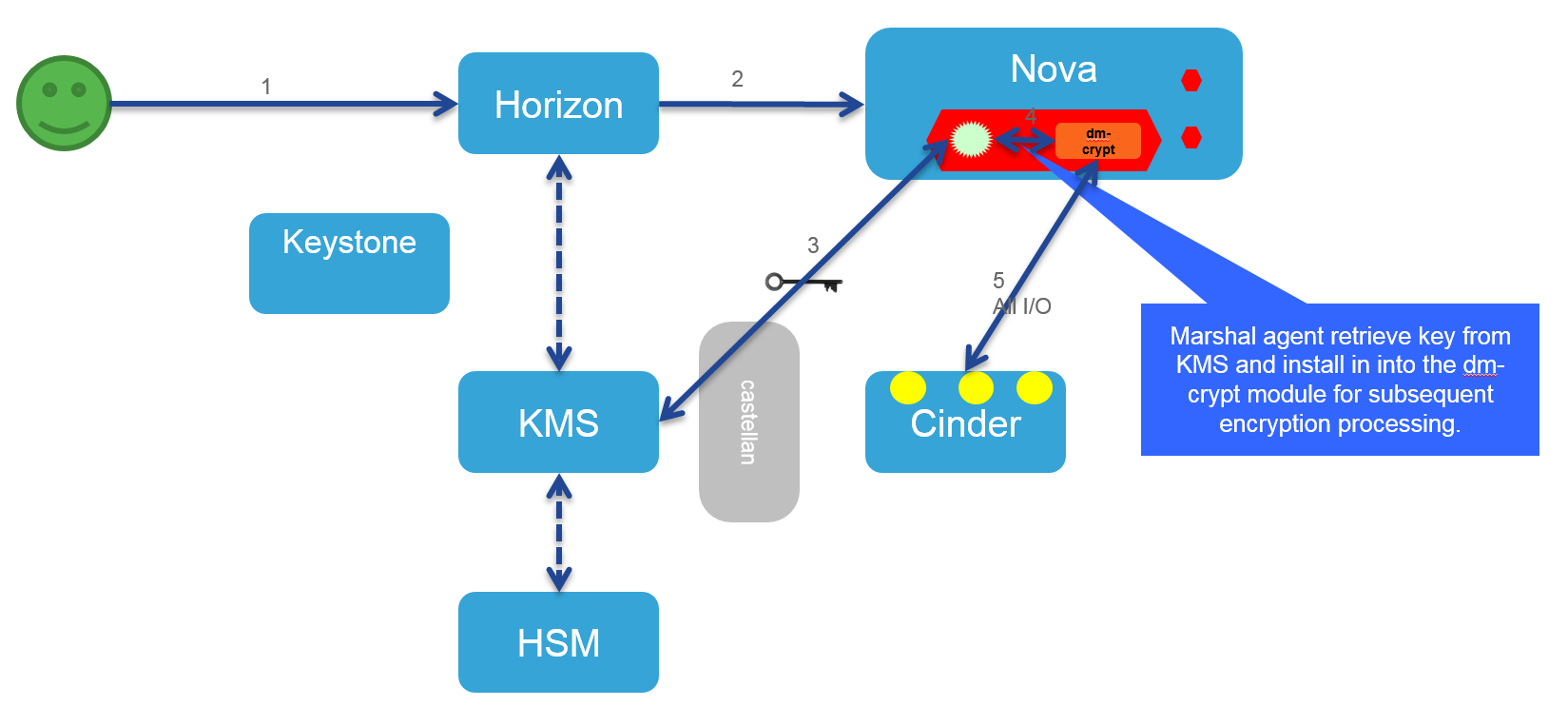
- Marshal is an agent service running inside virtual machines, which will be responsible for securely fetching encryption keys from ia KMS like Barbican.
- This agent will be interfacing with the disk encryption subsystem of the underlying operating system to encrypt/decrypt the disk I/O.
- In the case of Linux-based virtual machines this agent will be interfacing with dm-crypt and for Windows OS it will be interfacing with Bit-locker.
- The agent provides an abstraction service and can be integrated with other encryption subsystem as required.
- When the agent reads a key from the KMS, the key is only stored briefly in a secure temporary file until it can be transferred to the disk encryption subsystem.
Table of Contents
- Overview
- Features
- Architecture
- Getting Started
- Software Requirements
- Deployment Procedure
- Documentation
- Roadmap
- Core Components and Features
- Security
- Operations
- Platform Support
- Development
- License
Features
- Disk encryption subsystem abstraction allowing for a consistent interface
- KMS system abstraction allowing for a consistent interface
- Encryption at various levels including full disk encryption, partition encryption including root partition
Architecture
Getting Started
Deployment
#####For production purposes, Marshal is intended to be deployed as a Debian Package embedded into OpenStack VMs
Deploying Using Debian Package
Building and testing debian package
For test purposes, Marshal can be cloned using normal Git semantics:
Clone to local repository:
#####Via SSH:
$ git clone git@github.com:openstack/marshal.git
#####Via HTTPS:
$ git clone https://github.com/openstack/marshal.git
Software Requirements
- Python 2.7.8
- Cryptsetup (if Linux OS)
Deployment Procedure
Please refer to the Getting Started Guide, which covers deployment, configuration, and example usage.
Documentation
All documentation is located here
Roadmap
- KMS for infrastructure tenants
- Volume encryption (With Marshal)
- Certificate provisioning
- Object Encryption
- High key use tenants and IOT
- KMaaS
Core Components and Features
List core components and features here
- Orchestration
Security
List the security services it provides
- Encryption